Bitcoin Savings
Returning to the Simple Essence of Private Key Management
The storage of Bitcoin private keys is the most critical element in the entire cryptocurrency ecosystem. Over the past decade, countless investors have lost their digital assets due to improper private key management. This article will explore a well-thought-out Bitcoin private key storage solution designed for long-term savings. This solution is built on a comprehensive analysis of various threat models and takes into full consideration human weaknesses and real-world limitations.
Before discussing specific solutions, we need to clarify a key concept: Bitcoin private key storage is not just a technical problem, but a comprehensive challenge involving human nature, security, and usability. Any solution claiming to be "perfect" should be viewed with skepticism, as it often ignores the complexities of the real world. The solution proposed in this article is built on a deep understanding of human weaknesses while also considering the specific needs of different user groups.
Method
Simplicity is the ultimate sophistication.
Many people advocate engraving mnemonic words on stainless steel, titanium alloy, or other metal materials, believing this provides protection against water and fire. However, this method has serious security risks: text on metal materials is clearly visible under X-ray scanning. This means that anyone could potentially see your mnemonic words through security equipment when crossing borders. In comparison, writing mnemonic words on pages of a personal book is a safer choice - text on paper is almost unreadable under X-ray, and this method doesn't attract special attention. Once you reach your destination, you can easily recover your funds using any BIP39-compliant hardware wallet. Based on these considerations, this article proposes a simple yet reliable solution: dividing the Bitcoin private key into two independent parts - mnemonic words and passphrase, using different storage strategies for each. Specifically:
Paper can last for over 1,000 years. If you're concerned about water damage and fire, you can write multiple copies in different books. These can be kept in your home bookshelf, library, or relatives' homes. The advantage of books as storage media is that they are designed for long-term preservation, and under ideal conditions (avoiding direct sunlight, controlling temperature and humidity, preventing insect damage), paper can easily last over a thousand years. This is proven by the existence of ancient books that survive to this day. The mnemonic words use the most traditional pen and paper recording method, using ordinary paper and ink pen. This seemingly primitive method is actually the most reliable - under proper preservation conditions, paper records can last for thousands of years. The passphrase, on the other hand, relies entirely on brain memory, and this separation ensures that funds remain secure even if the mnemonic words are compromised.
At the implementation level, our recommendations are clear: For large Bitcoin savings, we recommend using Seed Signer as the signing device, paired with Sparrow wallet software. This combination achieves true air gap isolation and is completely open-source and verifiable. Remember, Seed Signer never stores any keys, requiring re-entry each time it's used - this is actually its design advantage.
Hardware choice considerations: Seed Signer, being completely open-source hardware, is ideal for long-term Bitcoin savings; while Ledger, with its broad ecosystem support, is more suitable for altcoin management. Both should use self-generated seeds for import rather than the device's built-in random number generator. This combination ensures absolute security for core assets while maintaining convenience. For managing other cryptocurrencies (altcoins), you can choose a Ledger hardware wallet, used with various Chrome browser plugins that support Ledger. Ledger's excellent ecosystem support ensures convenience in DeFi and other scenarios. However, remember that the passphrase in Ledger devices should only be entered temporarily, not stored permanently.
Regardless of which device you choose, one principle remains constant: always use self-generated seeds to import into devices, rather than blindly trusting the device's random number generator. This isn't about distrusting device manufacturers, but rather faithfully practicing the "Don't trust, verify" principle.
Air gap (physical isolation) is an extreme security measure where devices maintain physical isolation from the internet and other devices with network capabilities. This term originally comes from military and industrial control fields, such as critical systems in nuclear power plants that use air gap isolation. In the Bitcoin realm, air gap devices typically use QR codes, microSD cards, or handwritten data for physical information transfer, eliminating the possibility of remote attacks at the hardware level. For Bitcoin minimalists who adhere to the "Don't trust, verify" principle, devices like Seed Signer provide a path to building a completely verifiable system starting from the hardware level. These devices achieve complete air gap isolation, transmitting seed information through hand-drawn QR codes. While this method may seem cumbersome, it provides users with a completely transparent and controllable signing environment.
While the solution described above might seem simple, each technical choice contains profound considerations. To better understand this solution, we need to start from the most basic concepts and deeply analyze the principles and significance of each technical component. Let's first look at the origin of the Mnemonic Words concept.
Mnemonic Words: Making Random Numbers Memorable
Technology is best when it brings people together.
A Bitcoin private key is essentially a 256-bit random number. While this is perfect for computers, it's like hieroglyphics to human cognitive systems. During evolution, the human brain developed specific memory patterns - we excel at remembering concrete objects and emotional experiences, not abstract number sequences. This cognitive gap led to the creation of BIP39.
BIP39, which stands for Bitcoin Improvement Proposal 39, was introduced in 2013 and marks a significant milestone in Bitcoin's history. Through a carefully designed algorithm, it maps 256-bit random numbers to a library of 2048 carefully selected English words, ultimately converting them into groups of 12 or 24 words. This conversion maintains the original cryptographic security while greatly improving human memorability and writability.
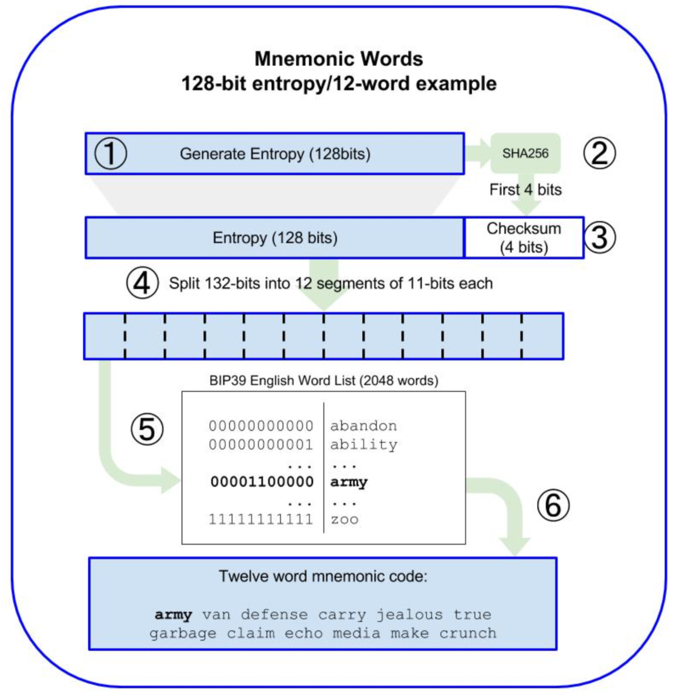 The mnemonic word generation process defined by the BIP39 specification.
Words come from the BIP39 standard wordlist, carefully selected:
each differs by at least 4 letters, avoids similar words, and can be uniquely identified by first 4 letters. For detailed implementation,
refer to Ian Coleman's BIP39 tool.
BIP39's core innovation lies in its clever balance between computer randomness and human memorability. As shown in the side diagram, the process converts pure random numbers into mnemonic words through SHA256 and lookup tables, maintaining cryptographic security while greatly improving usability. Each mnemonic word represents 11 bits of entropy, and with the final checksum, forms a complete cryptographic system.
The mnemonic word generation process defined by the BIP39 specification.
Words come from the BIP39 standard wordlist, carefully selected:
each differs by at least 4 letters, avoids similar words, and can be uniquely identified by first 4 letters. For detailed implementation,
refer to Ian Coleman's BIP39 tool.
BIP39's core innovation lies in its clever balance between computer randomness and human memorability. As shown in the side diagram, the process converts pure random numbers into mnemonic words through SHA256 and lookup tables, maintaining cryptographic security while greatly improving usability. Each mnemonic word represents 11 bits of entropy, and with the final checksum, forms a complete cryptographic system.
Each word in the wordlist represents 11 bits of information (2^11=2048), which explains why we need 24 words to securely store a 256-bit key (24 × 11 = 264 bits, with some used for checksum). This design ensures cryptographic security while accommodating human cognitive limitations as much as possible.
However, even a combination of 12 random words remains a significant memory burden for most people. These words have no semantic connection and don't form any meaningful narrative. Memorizing them is like memorizing a string of unrelated phone numbers, which goes against natural human memory patterns.
The solution to this problem comes from the concept of passphrase. It allows users to add a custom "25th word" to the mnemonic words. Unlike randomly generated mnemonic words, this passphrase can be any user-chosen string, providing possibilities for personalization and memorability.
The passphrase combines with the mnemonic words through the PBKDF2-HMAC-SHA512 function to generate the final seed. This means that even with the same mnemonic words, different passphrases will generate completely different wallets. This design cleverly implements "two-factor" protection: mnemonic words as "something you have," and passphrase as "something you know." This separation not only provides an additional security layer but also forms the foundation for designing a complete Bitcoin savings solution.
BIP39 Wordlist: 2048 Carefully Selected Words
The 2048 English words used in BIP39 were not randomly chosen but carefully selected. These words are relatively simple and common, and deliberately avoid easily confused similar words. For reference and use, here is the complete BIP39 wordlist:
It's a good practice to print out this wordlist and keep it safely stored. It can help you verify mnemonic words in an offline environment and can also be used for manual mnemonic word generation. Note that verifying mnemonic words online may pose security risks, so it's recommended to use offline tools or hardware wallets for handling mnemonic words.
Warning! Is Your Mnemonic Really Random?
God does not play dice with the universe, but when we need randomness, we should make sure we roll the dice ourselves.
In the Bitcoin world, there's a fundamental security issue that's often overlooked: where exactly does your private key come from? Even with the most secure hardware wallet, if its random number generator has been tampered with, all security measures become meaningless. This threat isn't just theoretical - there have been multiple cases in history where random number generators were found to contain backdoors.
Imagine this scenario: a hardware wallet manufacturer implements a special random number generation algorithm in their devices. On the surface, the numbers appear completely random, but in reality, all generated private keys come from a predetermined range. It's like a safe with millions of keys - seemingly secure, but the manufacturer might hold a master key.
Early dice generation methods attempted to generate BIP39 mnemonic words directly using ordinary dice. While mathematically correct, this method had serious practical issues: first, it required many rolls (about 5 per word), making it time-consuming and error-prone; second, users often resorted to online tools or programs to simplify the process, violating the air gap principle. Most importantly, the online tools themselves could contain malicious code, introducing new security vulnerabilities. This is why better solutions were later developed. Based on these security concerns, the Bitcoin community developed various physical random number generation methods. The earliest attempts used regular dice, but while theoretically viable, this method proved too complex and error-prone in practice. The community needed a solution that was both secure and practical.
 Entropia V2 "Austrian Edition" provides an elegant solution. This physical random number generation toolkit includes
the complete BIP39 wordlist and generates mnemonic words through physical extraction. Each dice is printed with
words from the wordlist, and users can build mnemonic phrases through multiple random draws. This method is not
only completely verifiable but also adds a ceremonial aspect to the private key generation process.
In this context, professional physical random number generation tools emerged. OpenPills provides such an open-source 3D printing solution. The core philosophy of these tools is to generate random numbers through visible, touchable, and verifiable physical processes, rather than blindly trusting electronic devices' random number generators.
Entropia V2 "Austrian Edition" provides an elegant solution. This physical random number generation toolkit includes
the complete BIP39 wordlist and generates mnemonic words through physical extraction. Each dice is printed with
words from the wordlist, and users can build mnemonic phrases through multiple random draws. This method is not
only completely verifiable but also adds a ceremonial aspect to the private key generation process.
In this context, professional physical random number generation tools emerged. OpenPills provides such an open-source 3D printing solution. The core philosophy of these tools is to generate random numbers through visible, touchable, and verifiable physical processes, rather than blindly trusting electronic devices' random number generators.
Physical methods of generating random numbers might seem "primitive" or "not high-tech enough," but this is precisely their advantage. These methods completely eliminate dependence on hardware manufacturer trust, implementing one of Bitcoin's core principles: "Don't trust, verify."
More importantly, the physical random number generation process has an unexpected benefit: it forces users to slow down and carefully consider each step of private key generation. This deliberately slowed process not only reduces operational errors but also helps users better understand the essence of Bitcoin private keys - they are just random numbers, and the quality of these random numbers directly determines your asset security.
Therefore, for users planning to hold Bitcoin long-term, carefully considering the source of private keys isn't optional - it's essential. Whatever physical random number generation method you choose, the important thing is to ensure the process is completely understandable and verifiable to you. After all, in the cryptocurrency world, your private key is your sovereignty, and this sovereignty shouldn't be built on trust in any third party.
Passphrase: The Digital Art of Misdirection
Deception in service of the greater good is not a fault—it is a feature.
The Shell Game, an ancient practice dating back to medieval Europe, demonstrates the art of protective deception:
a skilled operator presents multiple shells, with only one hiding the true prize. This centuries-old practice
inspired modern security concepts of "plausible deniability" - creating believable decoys to protect the real value.
This parallels Bitcoin's passphrase mechanism, where multiple valid wallets can exist, each appearing equally legitimate.
In cryptography, there exists the famous "rubber-hose attack" or "$5 wrench attack" dilemma: even the most complex encryption algorithms can't resist simple physical threats. Facing this challenge, Bitcoin provides an elegant solution through its passphrase mechanism, a design that could be considered the digital equivalent of the ancient Shell Game.
The passphrase serves as a "salt" in cryptographic terms, but its role extends far beyond traditional salting. Each different passphrase leads to a completely different key derivation path: Master Key = HMAC-SHA512(Key="Bitcoin seed", Data=Seed) where Seed = PBKDF2(Password=Mnemonic || Passphrase, Salt="mnemonic"+Passphrase) While a passphrase might look like a regular password, its mechanism is entirely different. Regular passwords are used for identity verification - enter the correct password, and you unlock specific content. However, a passphrase actually extends the mnemonic words, combining with them through the PBKDF2-HMAC-SHA512 function to generate an entirely new seed. This means each different passphrase generates a completely different wallet, rather than simply "locking" the same wallet.
Technically, the final seed generation process can be represented as:
Seed = PBKDF2(
Password = mnemonic_words || passphrase,
Salt = "mnemonic" + passphrase,
Iterations = 2048,
OutputLength = 512 bits
)
This design provides two crucial security features: First, there's no such thing as an "incorrect passphrase" - every passphrase generates a valid wallet, eliminating the possibility of brute-force detection. Second, even if the mnemonic words are compromised, funds remain inaccessible without the correct passphrase, providing an additional security layer. From a mathematical perspective, if an attacker obtains the mnemonic words, attempting to brute-force an 8-character passphrase containing uppercase and lowercase letters, numbers, and special characters would require trying (26 + 26 + 10 + 32)^8 ≈ 2.8 × 10^14 possibilities.
Based on this unique design, the passphrase not only provides additional security but also offers a viable defense strategy against physical threats: you can prepare multiple passphrases, each corresponding to wallets with different amounts. When faced with threats, you can reveal the passphrase for a smaller wallet as a decoy, both protecting your main assets and providing a plausible appearance of compliance. The key to this strategy is that all wallets are "real" - no one can prove you have other passphrases.
A passphrase can be any string, not limited to English words. This means you can use phrases that have special meaning to you, like a fragment of a poem or a life detail only you know the background of. This personalization not only enhances security but also greatly improves memorability. After all, human memory excels at storing meaningful information rather than random character combinations.
However, this powerful defense mechanism comes with a severe challenge: if you forget the passphrase, it means permanent loss of access to the corresponding wallet's funds. Unlike centralized services' "password recovery" function, in the Bitcoin network, there is no way to recover a lost passphrase. This requires us to carefully balance defensive capabilities with memorability when choosing a passphrase. Choosing a passphrase that is both secure and unforgettable might be the most carefully weighted decision in Bitcoin storage security.
 In June 2021, early Bitcoin participant Mircea Popescu died accidentally in Costa Rica, reportedly controlling up to 1 million bitcoins.
This tragic event reminds us that in the cryptocurrency world, key inheritance planning is as important as asset security.
Without proper inheritance plans, massive assets might be permanently locked on the blockchain, becoming "lost coins."
The Bitcoin community has witnessed too many cases of bitcoins being permanently locked due to lost keys or sudden accidents. This reminds us that a complete Bitcoin storage solution must consider not only security but also how to ensure assets can be retrieved by legitimate heirs in extreme circumstances. This requires designing a reasonable key inheritance mechanism while maintaining security.
In June 2021, early Bitcoin participant Mircea Popescu died accidentally in Costa Rica, reportedly controlling up to 1 million bitcoins.
This tragic event reminds us that in the cryptocurrency world, key inheritance planning is as important as asset security.
Without proper inheritance plans, massive assets might be permanently locked on the blockchain, becoming "lost coins."
The Bitcoin community has witnessed too many cases of bitcoins being permanently locked due to lost keys or sudden accidents. This reminds us that a complete Bitcoin storage solution must consider not only security but also how to ensure assets can be retrieved by legitimate heirs in extreme circumstances. This requires designing a reasonable key inheritance mechanism while maintaining security.
Passphrase Security: An Infinite Universe of Wallets
This is a real Reddit security challenge, demonstrating how difficult it is to crack a passphrase even with the mnemonic words and numerous hints. The eventual cracking process proved the limitations of brute force attacks. The passphrase is BIP39's most powerful yet often overlooked security feature. It's not just an additional password, but a magical key that can create infinite possibilities. Each different passphrase generates a completely new wallet from the same set of mnemonic words, creating an astonishing space of possibilities.
Let's look at a real case that occurred on Reddit: someone published a wallet's mnemonic words containing 0.0002437 BTC:
symptom few lift suspect hire visual oppose sustain merge drastic salmon requireThe challenger informed everyone that this wallet had a passphrase set and gradually provided the following clues:
- The passphrase is 20 characters long
- Contains special characters $ and !
- Contains letters y, g, r, and n
- Uses a total of 11 different letters
Even with this much information, very few people could crack the password over several months. The final password was proven to be "y0ulln3v3rgue$$thi$!". This process perfectly demonstrates the power of passphrases: even knowing it's 20 characters long, considering just lowercase letters, numbers, and two special symbols, the possibility space reaches (26+10+2)^20 - an astronomical number. In real usage, our passphrases can use any characters with unlimited length, creating a security barrier that's practically impossible to brute force.
Most importantly, a good passphrase doesn't need to be as complex as the example above. It can be a phrase that has special meaning to you, a unique life detail that only you know, or a distinctive memory. This personalization not only ensures security but greatly enhances memorability.
Just considering combinations of 11 English letters: 26^11 ≈ 3.67×10^15 possibilities. That's 36.7 trillion, or 0.367 quadrillion. To understand this scale: the Milky Way has about 100-400 billion stars, and this password space is tens of thousands of times larger than the galaxy's maximum star count. In other words, if you multiply the number of stars in the Milky Way (assume 200 billion) by over 10,000, you'd approach the scale of this total password count. Detailed calculation: 26^2=676, 26^3=17,576, 26^4=456,976, 26^5=11,881,376, finally 26^11≈3.67×10^15. When we discuss password complexity, even considering the simplest case - combinations of 11 lowercase English letters, the number of possibilities is astronomical. In practical use, since we can use uppercase letters, numbers, and special symbols, with no length restriction, the actual possibility space far exceeds this number. This is why a carefully designed passphrase is effectively impossible to crack through brute force.
Bitcoin Wallet Software Selection
Before discussing hardware wallets, we need to first understand a key software tool: Sparrow. This open-source Bitcoin wallet software not only serves as a unified interface for various hardware wallets but is also crucial support for implementing advanced security strategies.
To help users better understand Sparrow's functionality, here's a detailed tutorial:
This video demonstrates Sparrow's main features, from basic setup to advanced functionality usage. As an open-source Bitcoin wallet software, every feature of Sparrow is transparent and verifiable, which is crucial for building a trustworthy Bitcoin storage solution.
 Sparrow's interface design reflects its core philosophy: supporting advanced features while maintaining intuitive usability.
From multisignature to watch-only wallets, from single private keys to complete HD wallets, all these complex concepts
are integrated into a unified interface.
Compared to other wallet software, Sparrow has two notable security features: First, it uses Argon2 (the 2015 Password Hashing Competition winner) for key derivation, deliberately increasing computation time (at least 500ms on modern hardware) to resist brute force attacks. Second, it even encrypts public key (xpub) data - this seemingly excessive security measure is actually an important component of the "plausible deniability" strategy.
Sparrow's interface design reflects its core philosophy: supporting advanced features while maintaining intuitive usability.
From multisignature to watch-only wallets, from single private keys to complete HD wallets, all these complex concepts
are integrated into a unified interface.
Compared to other wallet software, Sparrow has two notable security features: First, it uses Argon2 (the 2015 Password Hashing Competition winner) for key derivation, deliberately increasing computation time (at least 500ms on modern hardware) to resist brute force attacks. Second, it even encrypts public key (xpub) data - this seemingly excessive security measure is actually an important component of the "plausible deniability" strategy.
In terms of functionality, Sparrow supports almost all mainstream hardware wallets, including Ledger, Trezor, Coldcard, and others. This broad compatibility isn't just simple aggregation, but provides a consistent user experience through a unified interface. Regardless of which hardware wallet users choose, they can achieve advanced wallet management functions through Sparrow.
For multisignature (MultiSig) wallets, Sparrow provides complete creation and management support. Users can mix different hardware wallets, providing not only manufacturer diversity protection but also flexible security strategy adjustment based on specific needs. For example, you can use Ledger to manage daily-use keys while using Coldcard to store backup keys.
More importantly, Sparrow supports complete descriptor wallets, meaning users can precisely control every technical detail of their wallet. This flexibility is crucial for implementing complex security strategies, such as creating sub-wallets for different purposes or implementing advanced inheritance planning.
What is a "Hardware Wallet": A Common Misconception
Before discussing hardware wallets, we first need to correct a common misconception. Many people view hardware wallets as devices for storing Bitcoin, similar to how traditional wallets store cash. This understanding is completely incorrect. From a technical perspective, what we call a "hardware wallet" is actually two completely different functional components: a signing computation device and a transaction broadcasting device.
The BIP44 specification defines the hierarchical deterministic path for HD wallets: m/purpose'/coin'/account'/change/address_index. However, some hardware wallet manufacturers have adopted their own derivation paths, such as Ledger using m/44'/60'/0'/0/0 for Ethereum, while Trezor strictly follows the BIP44 standard. While this difference might seem confusing, since all paths are open standards, any BIP39-compatible wallet can recover funds by adjusting the derivation path. For example, in Sparrow wallet, you can manually select different derivation paths to match specific hardware wallets. Using standard hardware wallets, assets can be recovered directly through the mnemonic words. Though different hardware wallets may use slightly different address derivation paths, these are all documented standard specifications, and through correct path settings, you can ultimately fully recover your assets.
The complexity of electronic devices directly affects their lifespan and maintainability. Even relatively simple Ledger devices will encounter various hardware issues after 10 years of use, such as LED screen failure. However, compared to smartphones, these issues can usually be resolved through simple component replacement. This is exactly why we need hardware design to be as simple as possible. When choosing a signing device, many people ask: why not just use an old iPhone? On the surface, an offline iPhone seems like an ideal choice: it has good security, a complete operating system, and an excellent user interface. However, this choice ignores a key issue: the complexity of electronic devices is inversely proportional to their maintainability.
An iPhone contains thousands of components, each of which could become a potential point of failure. When devices experience problems after 5-10 years, the difficulty and cost of repairs might make the entire solution unfeasible. In contrast, specialized signing devices (like Ledger or ColdCard) adopt a minimalist design: one security chip, a simple processor, basic display screen, and buttons. This simplicity not only improves reliability but more importantly ensures long-term maintainability.
This design philosophy tells us: when choosing a Bitcoin storage solution, we shouldn't be misled by current convenience. We don't need the most powerful device, but rather simple and reliable tools that can continue working steadily for over 20 years. In this sense, the design philosophy of hardware wallets is very similar to Bitcoin itself: simplicity is the most important feature.
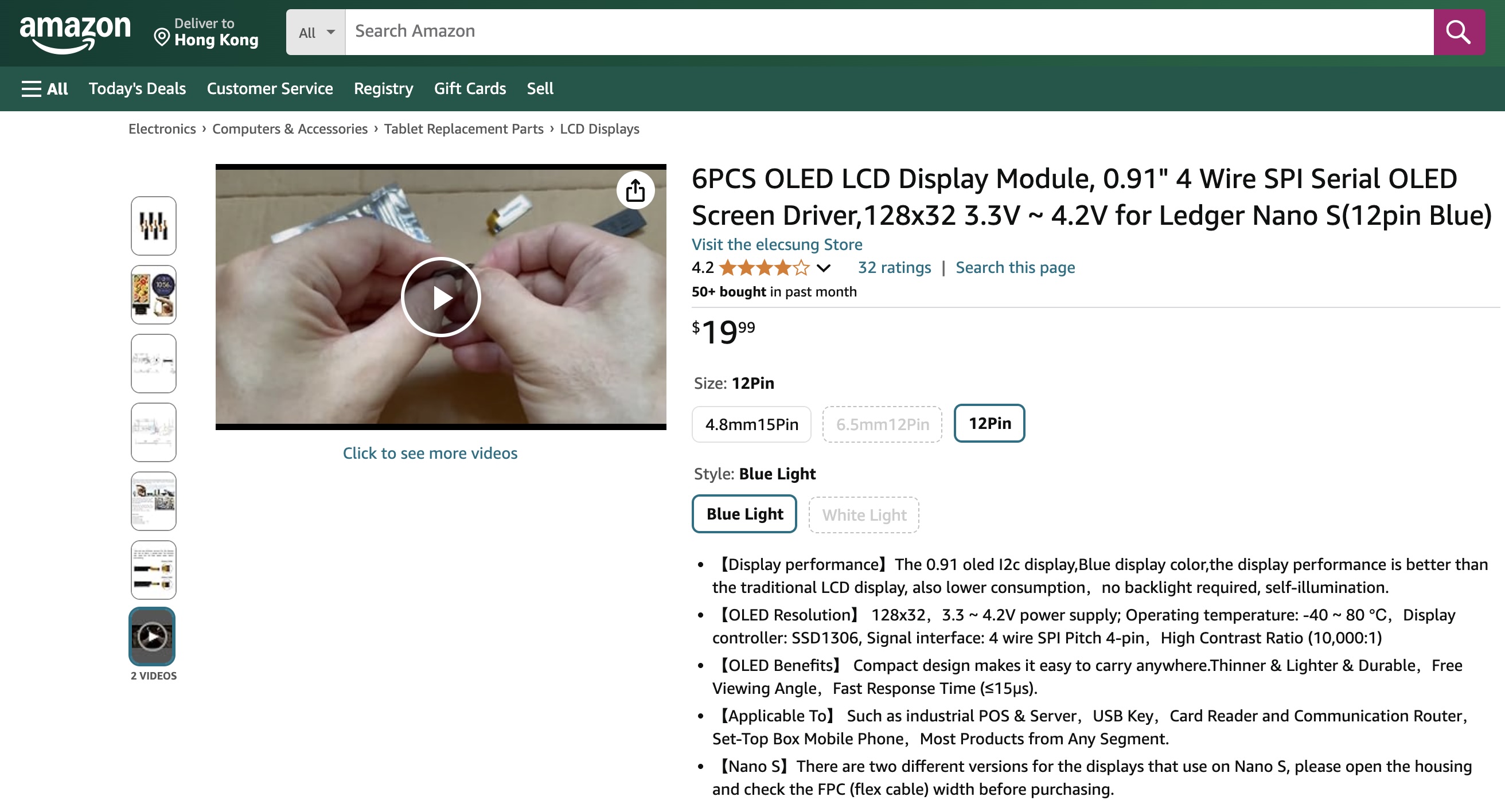 The Ledger Nano S LCD screen replacement kit is publicly available on Amazon,
complete with detailed repair video guides. This community-driven repair culture reflects Bitcoin users' pursuit of autonomy:
even for device repairs, they prefer to handle hardware wallets themselves rather than sending them to third parties.
This is where the value of simple hardware design lies - it allows ordinary users to perform basic maintenance.
The simplicity of hardware wallets reveals unique advantages in long-term use. Taking the Ledger Nano S as an example, when its LCD screen fails after years of use, users can completely repair it themselves. Considering the security properties of hardware wallets, sending devices back to manufacturers for repair could pose security risks, making self-repair the best choice. This repairability isn't accidental but stems from its modular and simple hardware design philosophy.
The Ledger Nano S LCD screen replacement kit is publicly available on Amazon,
complete with detailed repair video guides. This community-driven repair culture reflects Bitcoin users' pursuit of autonomy:
even for device repairs, they prefer to handle hardware wallets themselves rather than sending them to third parties.
This is where the value of simple hardware design lies - it allows ordinary users to perform basic maintenance.
The simplicity of hardware wallets reveals unique advantages in long-term use. Taking the Ledger Nano S as an example, when its LCD screen fails after years of use, users can completely repair it themselves. Considering the security properties of hardware wallets, sending devices back to manufacturers for repair could pose security risks, making self-repair the best choice. This repairability isn't accidental but stems from its modular and simple hardware design philosophy.
The Geopolitical Dilemma of Hardware Encryption
Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.
When discussing hardware wallet security, we face a rarely discussed but extremely important issue: all commercial hardware security modules (HSMs) actually come from very few countries. This is not coincidental. High-grade encryption technology has long been considered military equipment and is subject to strict export controls.
Currently, the security chips used in mainstream hardware wallets primarily come from these sources: ST31/33 series from France (used in Ledger), various commercial HSMs from the United States, and some NXP chips from the Netherlands. This highly concentrated supply landscape reflects not just technical barriers but also geopolitical realities. In today's consumer hardware wallet market, we mainly see encryption solutions from France (such as ST series chips used in Ledger) and the United States. While countries like Russia and China also have strong cryptographic research traditions and capabilities, their high-grade encryption technology is largely restricted to military applications and rarely seen in commercial products. This monopolistic market structure brings an unavoidable security concern: we must trust these mainstream encryption solution providers.
This creates a dilemma: completely open-source hardware solutions (like SeedSigner) are transparent and verifiable but cannot provide hardware-level key encryption protection; while solutions with encryption chips (like Ledger or Trezor) provide better physical security but inevitably introduce trust dependence on specific countries or companies.
More worryingly, these commercial encryption chips may all contain "backdoors." History has confirmed multiple times that some seemingly secure encryption solutions actually contained intentionally designed weaknesses. The famous RSA BSAFE incident is one example, where the NSA achieved decryption capabilities by planting backdoors in the standard.
This reality teaches us: when choosing and using hardware wallets, we can't blindly pursue any single feature. Both completely open-source solutions lacking hardware encryption protection and closed solutions providing hardware-level security have their limitations. True security often comes from a clear understanding of these limitations and using multiple protection mechanisms (such as passphrases) to compensate for the shortcomings of any single solution.
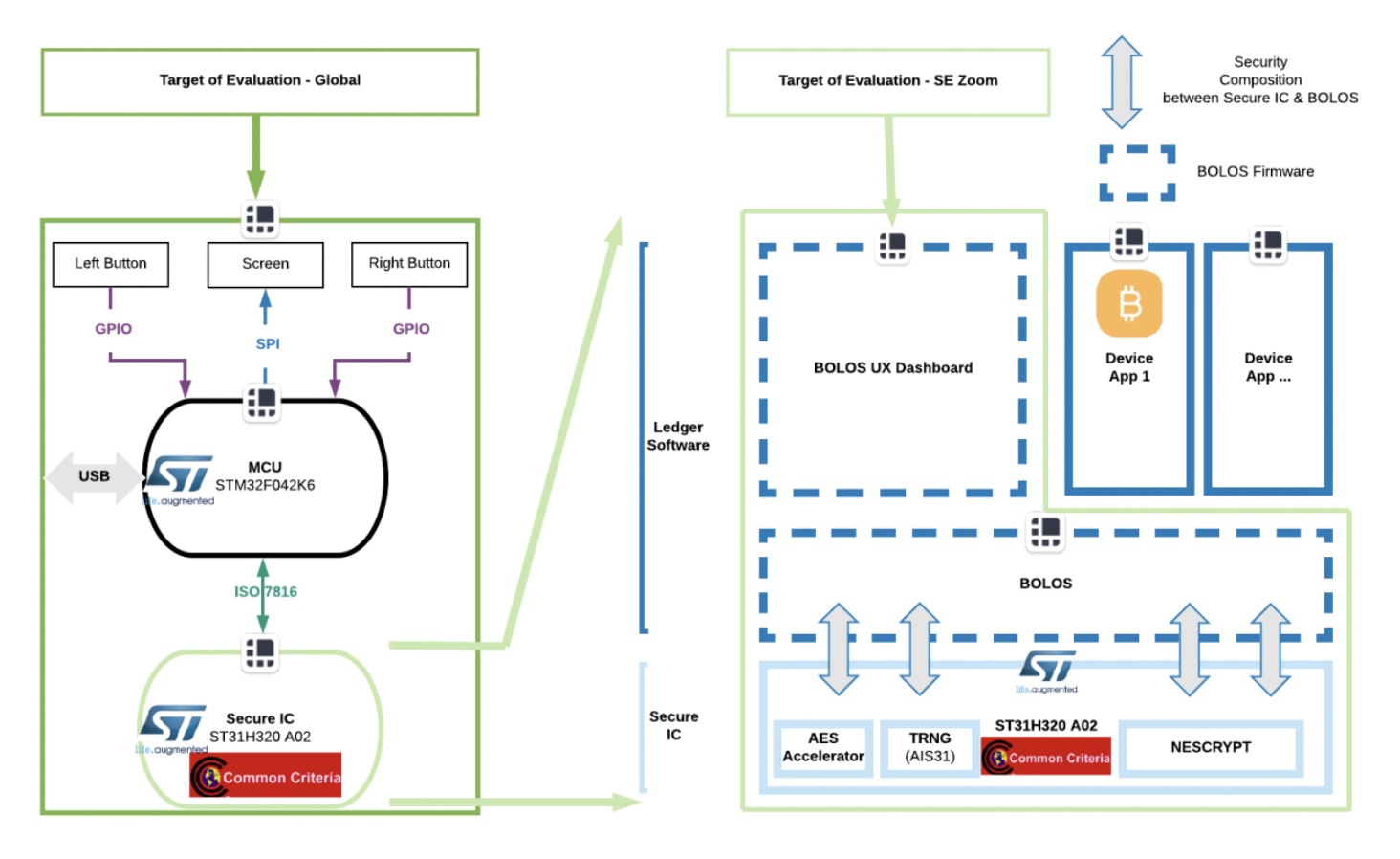 Ledger's dual-chip design: regular MCU (STM32F042K6) handles user interface and communication, while the security chip
(ST31H320 A02) processes all key-related operations. This isolation design communicates through the ISO7816 protocol,
ensuring keys never leave the security chip. The security chip has achieved Common Criteria EAL5+ certification from
France's National Cybersecurity Agency (ANSSI). In this diagram, pay special attention to the upper left section,
where each button represents an independent attack point.
Professional hardware security evaluation follows strict international standards. Taking France's CSPN (Security Certification of First Level) as an example,
this standard set by the French National Cybersecurity Agency
details every aspect of hardware security evaluation: from cryptographic algorithm implementation, random number generation,
to physical attack protection, all have rigorous testing requirements. This evaluation isn't one-time but an ongoing process,
ensuring devices maintain security throughout their entire lifecycle.
Ledger's dual-chip design: regular MCU (STM32F042K6) handles user interface and communication, while the security chip
(ST31H320 A02) processes all key-related operations. This isolation design communicates through the ISO7816 protocol,
ensuring keys never leave the security chip. The security chip has achieved Common Criteria EAL5+ certification from
France's National Cybersecurity Agency (ANSSI). In this diagram, pay special attention to the upper left section,
where each button represents an independent attack point.
Professional hardware security evaluation follows strict international standards. Taking France's CSPN (Security Certification of First Level) as an example,
this standard set by the French National Cybersecurity Agency
details every aspect of hardware security evaluation: from cryptographic algorithm implementation, random number generation,
to physical attack protection, all have rigorous testing requirements. This evaluation isn't one-time but an ongoing process,
ensuring devices maintain security throughout their entire lifecycle.
In Ledger's design, we can see several key features of professional encryption hardware: first is the physical isolation of security domains, completely separating regular operations and key operations through a dual-chip design; second is certified encryption algorithm accelerators (AES) and true random number generators (TRNG); finally, protection against physical attacks, including voltage fluctuation detection and temperature monitoring. These features cannot be achieved through simple software implementation but require specialized hardware design and manufacturing processes.
However, these certifications also create an interesting paradox: to pass security certification, chip manufacturers must disclose complete design details to evaluation agencies. This means that every certified security chip's internal implementation is fully known to at least one government agency. This brings us back to our earlier discussion of geopolitical issues: in pursuing hardware security, we must accept trust in specific institutions.
Hardware Wallet Choices and Trade-offs: Key Storage
Perfection is achieved, not when there is nothing more to add, but when there is nothing left to take away.
Currently, there are several well-known hardware wallet brands in the market, each with distinct chip choices:
- Coldcard: Uses ATECC608A security chip, a FIPS-certified encryption chip from Microchip
- Trezor: Evolved from early designs without encryption chips to the current Model T with integrated ST31H320 security chip
- OneKey: Chose a path similar to Ledger with ST31 security chips
Hardware Wallet Chip Comparison: 1. Coldcard: ATECC608A (Microchip) 2. Trezor Model T: ST31H320 3. Ledger Nano S: ST31H320 4. OneKey: ST31 series Each choice reflects the manufacturer's balance between security and usability. Among these choices, the non-Bluetooth, battery-free versions of Ledger Nano S/Plus are particularly recommended for the following reasons:
First, regarding maintenance difficulty, electronic device reliability is inversely proportional to its complexity. Lithium battery lifespan is usually the biggest weakness of hardware wallets, typically showing performance degradation after 2-3 years. Battery replacement not only increases maintenance costs but may also affect device water resistance.
Second, while Bluetooth technology is convenient, it has inherent security vulnerabilities that are difficult to completely resolve. Even the latest Bluetooth 5.0 protocol still faces threats such as man-in-the-middle attacks and replay attacks. The 2019 KNOB (Key Negotiation Of Bluetooth) vulnerability proved that even the most basic Bluetooth pairing mechanism could have serious flaws.
In comparison, USB communication, though seemingly "outdated," actually provides a more controllable communication channel. The USB protocol is completely open, and its security has been verified over decades. Of course, USB communication isn't completely risk-free, which is why we'll specifically discuss USB security details later.
Therefore, in hardware wallet selection, we should follow the principle that "simplicity is ultimate sophistication." The non-Bluetooth, battery-free design of Ledger Nano S/Plus achieves higher reliability and security by reducing potential failure points and attack surfaces. This design philosophy aligns perfectly with Bitcoin's own philosophy: for critical financial infrastructure, simplicity and reliability should take priority over convenience.
To better understand how Ledger's browser extension wallet works and its usage process, here's a basic video demonstration:
This video demonstrates Ledger's connection with Metamask. Through watching, you can clearly see how this hardware solution implements wallet (public key) import, and how its simple yet elegant design ensures private key security. Most importantly, the video shows how to use device signing to achieve completely offline transaction signing.
 Ledger Live provides an intuitive asset management interface, supporting various cryptocurrencies including:
1. Bitcoin
2. Ethereum
3. Stablecoins
4. Various DeFi tokens
The clean interface design makes it easy even for cryptocurrency newcomers to manage their asset portfolio.
Another significant advantage of the Ledger ecosystem lies in its seamless user experience. Modern cryptocurrency investors often need to interact with different Web3 applications, and Ledger provides extensive browser plugin wallet support through its WebUSB interface. Users can directly use hardware wallet signing in mainstream browser plugins like Metamask and Phantom. This level of integration far surpasses its main competitor Trezor.
Ledger Live provides an intuitive asset management interface, supporting various cryptocurrencies including:
1. Bitcoin
2. Ethereum
3. Stablecoins
4. Various DeFi tokens
The clean interface design makes it easy even for cryptocurrency newcomers to manage their asset portfolio.
Another significant advantage of the Ledger ecosystem lies in its seamless user experience. Modern cryptocurrency investors often need to interact with different Web3 applications, and Ledger provides extensive browser plugin wallet support through its WebUSB interface. Users can directly use hardware wallet signing in mainstream browser plugins like Metamask and Phantom. This level of integration far surpasses its main competitor Trezor.
Providing such a user-friendly experience while maintaining security is one of the key reasons why Ledger has maintained its leading position in the hardware wallet market. Whether viewing asset changes through Ledger Live or interacting with DeFi applications, users can enjoy a smooth and secure experience. This usability makes it an ideal bridge connecting traditional financial users with the cryptocurrency world.
However, it's worth noting that this convenience needs to be understood within the security framework. For large Bitcoin savings, we still recommend using completely offline methods, keeping daily transaction funds completely separated from long-term savings. Ledger's passphrase functionality provides ideal technical support for this separation.
Ledger Live as Ledger hardware wallet's companion software supports over 1,500 cryptocurrencies. Even with offline Nano S/Plus, you can monitor your assets by importing watch-only wallets. This design ensures private key security without compromising asset visibility. While this article primarily focuses on long-term Bitcoin savings, we must also acknowledge a reality: during bull markets, many people will want to increase their Bitcoin holdings by trading other cryptocurrencies (altcoins). In this scenario, Ledger's comprehensive ecosystem shows unique advantages.
Compared to hardware wallets focused solely on Bitcoin like Coldcard or Seed Signer, Ledger has built the most complete altcoin support ecosystem through its long history. This broad support isn't simple feature stacking but is based on the same security architecture: private keys for each currency are protected by the security chip, while supporting watch-only wallet functionality.
This design allows users to implement "coin-based" investment strategies without compromising security. For example, you can use altcoin trading to accumulate Bitcoin during bull markets while keeping your main Bitcoin savings completely offline. Ledger Live's watch-only wallet functionality makes executing this strategy simple and secure.
However, this convenience also brings additional complexity. Users need to clearly understand that: the more supported coins, the larger the software's attack surface. This is why we recommend separating large Bitcoin savings from daily trading cryptocurrencies, which can be achieved using different passphrases.
DeFi Risks: Learning from History
The December 2023 Ledger Connect Kit incident reminds us that even the most secure hardware wallets can face risks when interacting with the DeFi ecosystem. Attackers hijacked an npm package, causing approximately $600,000 in losses within just 5 hours. This incident proves the necessity of completely separating Bitcoin savings from DeFi interactions. While Ledger provides excellent multi-coin support, we must clearly recognize that any interaction with the DeFi ecosystem brings additional risks. These risks don't come from the hardware wallet itself, but from the complex DeFi ecosystem and various integration interfaces.
Taking the December 2023 Ledger Connect Kit incident as an example, attackers planted malicious code by hijacking a former employee's npm account. This incident affected multiple prominent DeFi projects, including:
- SushiSwap
- Phantom
- Balancer
- Other major platforms
Although the Ledger team deployed a fix within 40 minutes, it still resulted in losses of approximately $600,000.
This incident teaches us several key lessons:
- Long-term Bitcoin savings must be completely isolated from DeFi interactions
- Use different passphrases to separate wallets for different purposes
- Only use dedicated small-amount trading wallets for DeFi operations
This is exactly why we consistently emphasize: although Ledger provides convenient multi-coin support, main Bitcoin savings should be kept completely offline, avoiding any association with online services or DeFi protocols. Convenience and security often conflict, and when dealing with important assets, we must prioritize security.
Stateless Signing Devices: Returning to Bitcoin's Essence
Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.
Before understanding Seed Signer and other stateless devices, we need to rethink a fundamental question: do Bitcoin private keys really need to be "stored"? In fact, each transaction only needs to temporarily rebuild the private key at signing time, destroying it immediately after completion. This profound realization has led to a completely new hardware wallet design philosophy.
 Seed Signer's design is extremely simple: a Raspberry Pi Zero board, a display screen, and a camera.
This simplicity makes it a truly verifiable open-source hardware solution. Users input seed information
through hand-drawn QR codes, the device only temporarily rebuilds private keys during signing,
immediately clearing all sensitive data from memory afterward. This minimalist design ensures
users can fully control and verify every hardware component, achieving true air gap isolation.
Seed Signer embodies this design philosophy from its name to its implementation. It consists of two core parts: a hand-drawn QR code system for information input, and a simple computing device for signing. This design not only minimizes the attack surface but perfectly implements air gap (physical isolation).
Seed Signer's design is extremely simple: a Raspberry Pi Zero board, a display screen, and a camera.
This simplicity makes it a truly verifiable open-source hardware solution. Users input seed information
through hand-drawn QR codes, the device only temporarily rebuilds private keys during signing,
immediately clearing all sensitive data from memory afterward. This minimalist design ensures
users can fully control and verify every hardware component, achieving true air gap isolation.
Seed Signer embodies this design philosophy from its name to its implementation. It consists of two core parts: a hand-drawn QR code system for information input, and a simple computing device for signing. This design not only minimizes the attack surface but perfectly implements air gap (physical isolation).
The most striking feature of this design is that it stores absolutely no private keys or seed information. Each time it's used, users need to input seed information by scanning hand-drawn QR codes. This seemingly "inconvenient" design is actually an extreme security consideration: if the device itself stores no sensitive information, it cannot possibly leak such information.
The communication solution equally reflects minimalism: the camera is used to read transaction information and seed information, while the display screen shows transaction details to be signed and the final signature results. This one-way physical communication method fundamentally eliminates the possibility of remote attacks. More importantly, this design makes the entire device's behavior completely predictable and verifiable.
This design philosophy represents an important development direction for Bitcoin hardware solutions: rather than adding more security features to protect keys, it completely eliminates persistent key storage to avoid risks. While this solution sacrifices some convenience in usage, it provides a truly verifiable choice for users pursuing ultimate security.
This Bitcoin Magazine comprehensive guide covers the complete process from hardware procurement and assembly to specific usage. While the article is lengthy, considering it concerns your wealth security, it's worth taking time to read carefully. The article also demonstrates the advantages of open-source hardware solutions: every detail is transparent and verifiable. If you've read this far, you likely understand the core principles of secure Bitcoin private key storage. And Seed Signer, as a completely open-source signing device, perfectly embodies these principles. If your goal is long-term Bitcoin holding, I strongly recommend spending a few hours carefully reading and considering the above guide before taking action. Investing time in learning and understanding is much wiser than blindly pursuing quick action. After all, in the cryptocurrency world, ignorance is often more dangerous than carelessness.
To better understand SeedSigner's working principles and usage process, here's a basic video demonstration:
This video demonstrates SeedSigner's complete build and usage process. Through watching, you can clearly see how this open-source hardware solution achieves true air gap isolation, and how its simple yet elegant design ensures private key security. Most importantly, the video shows how to achieve completely offline transaction signing through hand-drawn QR codes.
On Multisignature and Key Sharding: A Sober Assessment
Complexity is the worst enemy of security.
Multisignature and MPC technologies' main application scenarios are institutional and team management, such as: 1. DAO organization fund management 2. Corporate fund governance 3. Other group control situations In these scenarios, multi-party control can indeed provide additional security safeguards, as different parties can check and balance each other. When discussing Bitcoin storage solutions, multisignature (Multisig) and multi-party computation (MPC) are often viewed as ultimate solutions for enhancing security. However, this perspective might be misguided in personal savings scenarios.
First, we need to understand a basic fact: whether it's a single 24-word mnemonic phrase or two sets of 2-of-3 multisig mnemonics, neither can be reliably memorized by the human brain. This means they all require physical storage, and the security of this physical storage is the real key. When facing physical threats, holding two sets of 24-word mnemonics is not more secure than holding one - in extreme cases, attackers can obtain all physically stored information.
More importantly, multisig and MPC solutions typically increase scheme complexity. Each additional signing device or key shard means adding another component that needs secure storage and management. This complexity not only increases the risk of operational errors but might also lead to the collapse of the entire scheme due to oversight in one component.
For personal savings, a well-designed single-signature solution (combined with passphrase and appropriate physical security measures) is usually sufficient. This not only reduces scheme complexity but also avoids potential mistakes that might occur when managing multiple keys. Security often lies not in adding more layers, but in perfecting the most basic components.
However, this doesn't mean multisig and MPC have no value. On the contrary, these technologies are extremely important in specific scenarios: when dealing with team, institutional, or collective asset management, multisig provides necessary governance mechanisms. In these scenarios, the mutual checks and balances between different participants can truly leverage the advantages of multisig.
For personal savings, a well-designed single-signature solution is often the best choice. This is not only because it's simple and reliable but more importantly because it avoids human errors that might occur when managing multiple keys. In the Bitcoin world, the design principle "less is more" is particularly important.
Bitcoin Inheritance: Simplifying Estate Planning Through Digital Design
In the digital age, the true measure of technology lies not merely in amplifying today's efficiency, but in forging a lasting pathway of wealth and knowledge for generations to come. If we harness innovation only to accelerate the present without ensuring its inheritance, all we achieve may eventually slip into oblivion.
The most famous case is early Bitcoin participant Mircea Popescu, who tragically drowned while swimming at a Costa Rica beach in June 2021. He reportedly controlled up to 1 million bitcoins, which may be forever locked on the blockchain. Similarly in June 2023, a group of Amazon employees perished in the Titan submersible incident, including individuals holding significant cryptocurrency holdings. These tragic events remind us that death often comes unexpectedly, and without proper inheritance planning, vast digital wealth can disappear forever. All the technical solutions we've discussed earlier ultimately face a practical issue: how to ensure these digital assets can be passed on to the next generation? This question is crucial because Bitcoin, unlike traditional assets, has no centralized institutions to assist with inheritance. If private keys are lost, these assets will be permanently locked on the blockchain. Bitcoin's history has witnessed too many cases of huge assets being permanently lost due to accidents. These cases remind us that inheritance planning isn't optional - it's essential.
In the traditional financial system, inheritance has complete legal frameworks and execution mechanisms. But in the Bitcoin world, if private keys cannot be transferred, even the most perfect will is useless. This is why our solution must be simple enough to be reliably transmitted in life's final moments. Some suggest using complex multisignature schemes, but consider this: in that moment, would you be able to clearly explain these complex technical details? In this context, our previous emphasis on passphrase simplicity becomes particularly important. An ideal passphrase should:
- Be easy to remember and transmit
- Have special personal significance
- Be clearly expressible in emergency situations
In fact, the passphrase can serve as your "last words." While mnemonic words can be physically passed down through generations (such as being saved in books), the passphrase can be verbally transmitted in the final moments. It's this simplicity that ensures wealth can be smoothly inherited in life's critical moments.
This also reminds us that when designing Bitcoin storage solutions, we must consider not only security but also inheritability. Overly complex solutions might fail due to inability to transfer, while simple and elegant solutions are more likely to stand the test of time. Just like Bitcoin's own design, true wisdom often manifests in the ability to simplify complex problems.
Conclusion
The devil is in the details.
As Mies van der Rohe noted, the devil truly is in the details. In the practice of Bitcoin security storage, many critical technical details require professional guidance:
Critical Technical Details:
- Hardware Wallet Import Details
- When recovering with Ledger, should you choose 12 or 24 words?
- Why does Ledger Live show "Import Successful" but zero balance?
- How to verify if the imported mnemonic is correct?
- Temporary Passphrase Management
- Should the temporary passphrase be stored in the device or re-entered each time?
- How to verify if the passphrase is correctly active?
- How to migrate passphrase settings when changing devices?
- Derivation Path Issues
- Why do identical mnemonics show different addresses in different wallets?
- What's the path difference between native segwit and nested segwit?
- How to ensure address consistency when switching wallet software?
- Transaction Broadcasting and Node Selection
- How to safely broadcast offline-signed transactions?
- What are the differences between Electrum nodes and full nodes?
- How to verify node reliability?
- Privacy implications of private vs. public nodes?
- Privacy Protection Strategy
- How to avoid address reuse?
- What is CoinJoin and how to use it safely?
- How to prevent transaction graph analysis?
- How to use PayJoin for privacy protection?
- UTXO Management and Transaction Fees
- How to effectively manage UTXOs to reduce future transaction costs?
- How to select optimal transaction fees?
- Security strategies for change addresses?
- How to handle dust attacks?
- Mobile Configuration
- Mobile solutions compatible with Sparrow
- How to ensure mobile wallet security?
- Safe interaction between cold and hot wallets?
- Watch-only Wallet Setup
- How to safely export/import public key information?
- How to synchronize multiple watch-only wallets?
- How to prevent privacy leaks from watch-only wallets?
- Emergency Preparation
- Contingency plans for hardware wallet failure
- How to prepare secure backup devices?
- Asset access strategies during international travel
Each of these details can impact your asset security. A seemingly simple misconfiguration could lead to:
- Inaccessible funds
- Unnecessary transaction fee waste
- Privacy breaches
- Security vulnerabilities
I offer the following professional consultation services:
- Customized security strategies based on your specific needs and risk profile
- Step-by-step guidance for hardware wallet setup and configuration
- Best practices for UTXO management and privacy protection
- Security strategies for node setup and transaction broadcasting
- Inheritance planning tailored to your family situation
- Review and audit of existing security setups
For professional consultation, please contact:
- Email: william.yang@trustlessenterprise.com
- Available for both remote and in-person consultations
- Customized solutions for individuals and organizations
- Strict confidentiality guaranteed
Remember: when it comes to securing significant Bitcoin holdings, the cost of professional guidance is minimal compared to the potential risks of improper setup. Your digital assets deserve the same level of professional care you would give to any other significant investment. In digital asset security, every detail matters. Professional guidance not only helps you avoid potential risks but also enables you to truly understand and control the security of your digital assets.